Welcome Avatar!
If there’s one DeFi Education prediction that stands out above all for 2022, it’s that the lawyers are coming. We’ve been covering the major regulatory issues all year for paid subs.
This week there’s been a big fuss on Crypto Twitter about Infura/Metamask’s new privacy policy: IP addresses and Ethereum addresses are “collected”.
If there’s one thing we know, it’s that Crypto Twitter is extremely emotional. In fact, Crypto Twitter’s emotions exhibit about as much reflexivity as crypto assets themselves.
It’s no wonder that Crypto Twitter participants jump from honeypot to honeypot, scam to scam, false idol to false idol.
We would not be surprised to find out there are people out there who lost money on each of Frog Nation, Sifu, Do Kwon, 3AC, BlockFi, Celsius, and FTX all in ~6 months.
We are convinced at this point: most people will never learn. And outside of DeFi Ed subscribers, we’re pretty much done trying to convince them. It’s not WAGMI anymore, it’s “those who obtain the right resources, apply what they learn and are discerning about who to listen to will make it.”
Anyone can write some Twitter threads and get a bunch of people who don’t know any better to follow them. Then people think because someone has followers they are “credible.” If that’s how you think, this is your fate:
Markets are adversarial. Don’t be the sucker at the table.
This is your final wake up call. 👇
✓
On to today’s topic.
In a past life, one of our writers led organization-wide InfoSec.
We’ll will give you the context you need to evaluate the Metamask / Infura news. Then we’ll give the technical information on how to solve the Ethereum RPC privacy problem correctly.
How Companies Really Think About Privacy
How companies store and use customer data is governed in the European Union by the General Data Protection Regulation (GDPR). Other countries are developing or have implemented similar privacy laws.
We’re using GDPR as a jumping off point because of the wide-ranging changes its adoption forced in both European and multinational corporations, the significant penalties for non-compliance, and personal experience updating corporate IT systems for the change.
GDPR Privacy Requirements
Lawfulness, fairness, and transparency
Purpose limitation: only use personal data for specified and legitimate reasons
Minimization: data must be adequate, relevant; and limited to what is necessary
Accuracy: up to date and amended / deleted where necessary
Storage limitation: retain data only as long as necessary
Integrity and confidentiality: take technical and organizational measures to secure data against unlawful processing and accidental loss
Consequences for Breach
Fines up to 4% of *global turnover*. Amazon Europe was assessed a EUR 750 million fine. (~US$800 million)
Corporate Directors can be held *personally liable* for breaches
National laws also typically impose criminal penalties for certain breaches of privacy laws, in some cases “recklessness” rather than willful intent is sufficient to attract criminal liability. Corporate Directors can also be held criminally liable.
Being sanctioned for a privacy breach can trigger termination clauses in commercial contracts and can impact success when tendering for new contracts
TLDR: Failing to meet privacy requirements can have HUGE consequences.
Assuring Compliance
Complying with privacy legislation can be very expensive. Organizations take it very seriously: expensive IT overhauls, senior staff invest a ton of time, expensive training courses and hiring compliance professionals.
Budgets are set according to business size and risk, considering:
Number of employees
Assets
Revenues
Business activities
Value and complexity of transactions
Industry benchmarks
Geographical extent of the business
Whether the industry is regulated
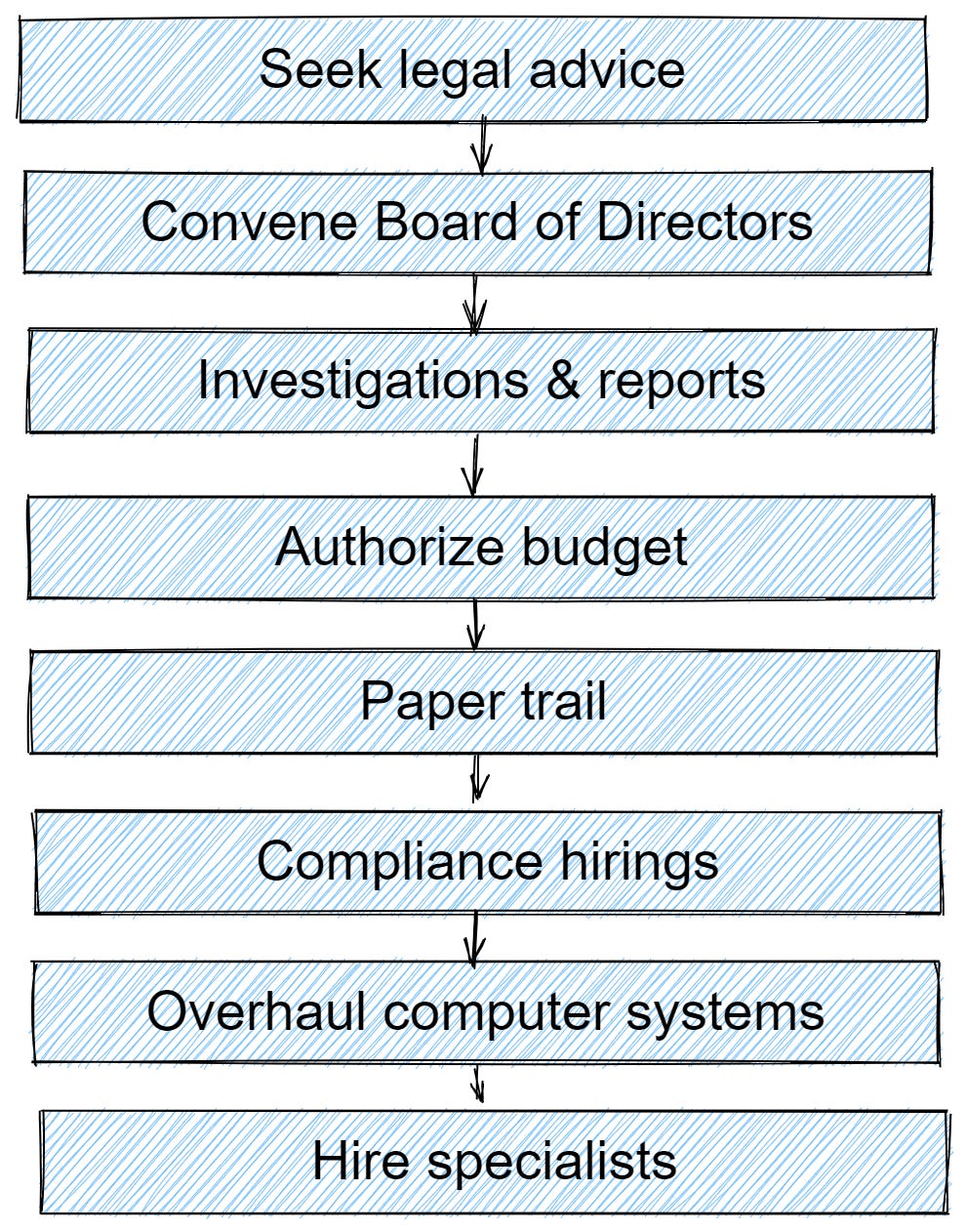
When a company becomes aware that it is subject to privacy regulations (due to changes to the law, how the business operates, or quite commonly as the result of discovering a compliance gap) they typically need to do the following:
It’s no small undertaking, and often involves the highest levels of an organization. One of the key responsibilities in data protection compliance is drafting and updating privacy policies. These must accurately reflect how the organization processes data.
Why are we telling you all this?
Metamask and Infura
Metamask is the popular browser extension which provides wallet services and allows you to interact with dApps. Infura provides Remote Procedure Call services to Metamask - a fancy way of saying that it allows Metamask to look up data from the blockchain (token balances) and submit transactions. Both Metamask and Infura are owned by the same company, Consensys.
Key points to understand:
Metamask can’t work without talking to an RPC node
All public RPC nodes are technically in a position to monitor your IP address and wallet address
Whenever you load Metamask it fetches all your address token balances from Infura’s RPC by default, so even if you made 10 different addresses Infura knows you own them all (you looked up all 10 at the same exact moment from the same IP)
Depending on Consensys’ data retention policy, IP and address information (and other data) may be available to civil courts and law enforcement
*All* wallet providers work in this way. Without public RPC infrastrucutre providers, Ethereum users would need to run a full Ethereum node on their device.
A change to the Consensys privacy policy has drawn a lot of attention this week.
Information collected by Infura when you use Infura as your default RPC provider in MetaMask.
https://metamask.io/
(“MetaMask”) and https://infura.io/ (“Infura”) are both products offered by the Company and Infura is the default Remote Procedure Call (RPC) provider in MetaMask. When you use Infura as your default RPC provider in MetaMask, Infura will collect your IP address and your Ethereum wallet address when you send a transaction.
We went into the dry legal details above to underscore how expensive it is for an organization to collect *any* data. The old “grab everything” approach has been replaced with a nuanced analysis which minimizes data collection, anonymizes data where possible, and clearly links data retention to legitimate business purposes.
So why “collect” Ethereum addresses and IP addresses?
You can’t receive data over the Internet without knowing the sender’s IP address. All companies which operate web services need to collect this data and are obliged by law to disclose this in their privacy policies. So far, normal.
The Ethereum address is collected because it’s part of the transaction data which needs to be sent to the mempool to be included in the next block.
The real questions are:
Are these records discarded immediately or retained for some short period to enable technical troubleshooting?
Or, is Consensys creating an internal database which matches IP records to transaction records, storing it for an indefinite period, and making it available in response to law enforcement requests or court orders?
The policy is silent on these points. Our *guess* is that they’re just disclosing what is technically necessary and there’s no broader conspiracy to collect data. But. You shouldn’t be sharing data with third parties. You can use free and secure privacy tools so that you don’t share your IP address or other potentially identifying information with any service provider.
Even if your wallet provider claims not to collect any data, why should we believe them?
Why Now?
A common reason for updating a privacy policy is the result of a “gap analysis” which compares the documented policy with actual practice. A routine data privacy audit can reveal that an organization has been collecting data or using it for purposes which have not been disclosed as required in the privacy policy.
We don’t know if this was the case with Consensys, but it would be a reasonable guess that such data was normally collected for technical reasons and the company is updating their policy wording due to recommendations from a privacy review.
We’ve seen people state on Twitter that Metamask has ‘begun collecting IP addresses’ and there doesn’t seem to be evidence for this. Or for the speculation that law enforcement or regulators have ‘leaned on’ them to start collecting data.
But. You shouldn’t trust third parties.
Autist note: if you’ve *ever* used Metamask, assume that your Ethereum addresses and transactions are linked to the IP address you used. Not necessarily by Consensys. And we doubt this was a recent technical change to ‘install monitoring’.
“Just change your RPC provider bro”
Well, no. You’d be swapping out Infura for another provider (Alchemy) who you are also trusting not to log / share your data. What about a provider like Pokt which claims to support decentralization? Too bad, they’re a US company with servers in the US and made their position perfectly clear when OFAC sanctioned TornadoCash:
Using a VPN works. But. You might not want your anon identity linked to all of your crypto holdings either. In this case it makes sense to use a separate VPN to transact from the VPN you use for Discord, Twitter, and general crypto browsing. But if you’re using two or more VPNs on the same PC you are likely going to link the identities because of unique hardware, monitor layout, browser version, and so on. We covered “browser fingerprinting” in detail: