Welcome Avatar! From January 2021 to March 2022, over 46,000 people reported losing over $1 billion in crypto to scams. The median loss per individual was a whopping $2,600.
Bad crypto security is expensive. The sinking feeling of watching the money leave your wallet, never to return, sucks.
Since crypto hacks and scams are so profitable, hackers and scammers are getting smarter and more sophisticated.
Cryptocurrency users and business owners are at risk of having their computers hacked, which can lead to the theft of sensitive information and huge financial losses.
Here are some common attack vectors:
Phishing Scams: Phishing scams are email or web-based attacks that trick users into revealing their personal and financial information. These attacks can be disguised as legitimate messages from banks, payment processors, or other trusted sources. Clicking a link or opening an attachment can permanently compromise your computer, even affecting transactions you sign with Metamask
Malware: Malware is malicious software that is designed to cause harm to a computer or steal sensitive information. Malware can be spread through email attachments, downloaded files, or infected websites. Browsing a crypto site with a zero day exploit can permanently compromise your computer.
Unsecured Wi-Fi Networks: Using public Wi-Fi networks, such as those in airports or cafes, can be risky as they may be unsecured and easily compromised by hackers. Using a VPN properly avoids this threat.
Outdated Software: Running outdated software, such as an outdated web browser, can leave a computer vulnerable to security exploits. And. Zero day exploits can permanently compromise your computer even if you’re up to date.
Our team implements an in-depth approach to security backed by over a decade of IT security experience. This includes
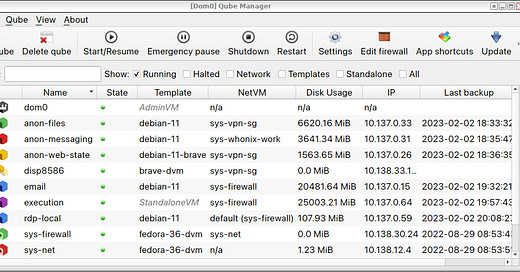
Security by isolation: keeping personal data and internet activities strictly separate from our anon online profiles
When working in crypto we keep each client’s data segregated and our use of crypto wallets is done in yet another container
Sandboxed web browsing: when we’re visiting untrusted websites, we use a virtual machine sandbox that doesn’t store changes, so any browser exploit doesn’t persist the next time we use the computer, or across contexts
Secure VPN: to avoid hacked Wi-Fi networks (even at home)
We’ve done our best to put forward security best practices and provided both technical and non-technical solutions.
But.
These techniques are difficult to set up and use if you’re not a security expert. Security is important to us and the last thing we like to hear is that people lost money despite our training and guidance because it was too complex to set up.
After a lot of brainstorming we thought: what if we could get you a computer set up just like ours for security? One that was put together by our security expert Iguana?
Such a computer would mean you can be confident that your data is secure, your VPN is leak-proof and your computer is hardened against many types of cyber attacks. And. Your regular tasks will become easier to do securely, thereby saving you time.
Our customized laptop would allow everyone to easily benefit from our years of research and customization efforts.
While we find it hugely valuable, we understand that a fully secure setup may not be a fit for everyone. Before we finalize product development, we want to get a sense for how many people want to solve security once and for all.
We’ll lay out the details and leave a quick form at the end to fill out for those who would like to be part of the waitlist.
Important: There is no $ commitment at this stage but please only sign up if you are seriously interested.
Reasons It’s Not For You
We value your time so we’ll list all the reasons it may not be for you first. None of these would be dealbreakers for us for a dedicated crypto laptop, but we want to be upfront about the tradeoffs.
You’ll Need a New Laptop
We will be customizing the Qubes security operating system for you. Qubes lets you run security hardened instances of Windows and Linux while keeping your data securely stored in separate virtual containers.
However, proper functioning can only be guaranteed on specific devices.
We have found a quality vendor who offers user-upgradable laptops. To ensure this works you will have to purchase a laptop from this vendor. The benefit is that if you go with this new laptop, it should be the last one you will ever need which saves you money in the long run. More on this later.
It Can’t Run Apple Mac Software
Unfortunately there is nothing we can do about this.
This setup is not Mac compatible. If that’s a dealbreaker for you, we’d still recommend having a separate secure laptop for crypto but our solution is not currently available for Macs.
No 3D Accelerated Games (or rendering)
Did you know that standard operating systems allow a program to read information off the screen from other programs? Meaning, if you run a program it can see everything else on your screen. This is a major security risk.
To mitigate this threat, you have to prevent programs from directly accessing the graphics card. But. That means 3D acceleration for gaming (or video rendering) isn’t available. Crypto browser-based games like DeFi Kingdoms should be fine.
Who Should Use This?
Our view is that developers, executives, business owners, and basically anyone responsible for other people’s funds need to have this setup or something equally as secure. It’s one thing to take risk with your funds, another thing entirely when you’re entrusted with overseeing the funds of others (not to mention the potential legal risk).
As an owner or operator, your business information is a target for both competitors and cyber-criminals. You may owe legal duties towards your customers or third parties to project confidentiality. No shortcuts if this is you.
For developers, you’ll be able to:
easily run multiple operating systems and diverse build environments
securely separate different projects, reducing the risk of data breaches
access copy-on-write OS templates, easily revert to a known good config
career development - knowledge of virtualization & security is in high demand
For the less technical people, this is as close to a plug-and-play solution to crypto security as you’ll get.
For everyone else, we will leave it up to you on how much you care about your security and privacy. In our view, if you currently have or plan to have over ~$50K in crypto assets in the future, we think this investment is more than worth it.
Selected Features
The solution will be put together by our security chief BowTiedIguana.
We’ll send the line by line detailed technical specs to those who join the waitlist, but here is the birds’ eye view.
Modular laptop: It will most likely be a modular laptop, meaning parts can be easily upgraded and repaired. This means the laptop lasts for much longer and saves you money in the long run. We’re currently in discussions with a vendor (hence “most likely”)
QubesOS: QubesOS is a highly secure yet user-friendly operating system endorsed by experts (including Edward Snowden)
Fail-closed VPN tunnel: all network traffic is directed through the VPN, even in the event of a VPN failure. This helps to protect the user's privacy and security by preventing sensitive information from being transmitted over the internet unencrypted. And it still works if a malicious software in one virtual machine is actively trying to discover your real IP address (other solutions don’t do this).
Integrates with Whonix and Tor: Whonix is highly secure privacy software which runs inside QubesOS and Tor is a privacy network - a replacement for VPNs - originally designed by the Navy.
Whonix and Tor provide users with a range of security features that help to protect their privacy and security when using crypto and the internet
These technologies are ideal for people who are concerned about online surveillance, data breaches, wallet tracking, phishing or other privacy and security threats
Offline virtual machines: users will be able to create and run virtual machines that are isolated from the internet and other network connections. This helps to protect sensitive information, such as private keys, from being stolen or leaked over the internet.
Automatic Encrypted Backups: Qubes supports backing up individual virtual machines, templates, and the entire install (all data and applications) in an automatically encrypted format. Backup targets can be external USB hardrives or even cloud storage.
TLDR: Highly secure and private laptop for your crypto needs.
Can I Do This Myself?
Anyone can purchase a modular laptop with hardware configured to their preference. The QubesOS system is open source and can be downloaded and installed by anyone.
If you’re an advanced user who understands IT security and is familiar with administration of Linux, you can do this yourself.
QubesOS takes hours to customize for crypto, even for advanced users familiar with the environment. You’d save significant time and hassle with our bespoke installation. If you’re not an advanced user you’re in for a rough time going all the way alone.
DIY saves you a few hundred dollars, at the cost of time to set up. If you’re not a proficient Linux user you might find the process frustrating.
Buying from Us
Ease of Use: Our system is designed to be easy to use, with software already installed and configured. Iguana has been using Qubes for a decade.
Support: You’ll receive access to a support channel where you can ask questions about security best practices and troubleshooting (excluded for barebones option).
Quality Assurance: We’ll test that the hardware and software are working correctly together.
Spec & Cost
fast Intel i7 processor with Performance and Efficiency Cores
32 GB of RAM, enough capacity to run a dozen virtual machines smoothly
1 TB NVME SSD storage
QubesOS and access to our support channel
Est. ~$2,499 US Trash Token + taxes & shipping
Custom Options
We can accommodate bespoke hardware configurations, reach out for a quote.
Please allow a longer lead time for custom builds.
How To Order
Please enter your email to receive technical specs HERE.
Order forms will go out when testing of the product is completed.
Disclaimer: None of this is to be deemed legal or financial advice of any kind. These are opinions from an anonymous group of cartoon animals with Wall Street and Software backgrounds.
We now have a full course on crypto that will get you up to speed (Click Here)
Security: Our official views on how to store Crypto correctly (Click Here)



Fantastic idea guys/gals/whatever. Great way to expand the brand beyond the stack and defi academy.... best of luck!
I run Qubes and my impression is that their greatest accomplishment is that it’s easy to use multiple VMs once you get it set up. Setting it up right is way beyond average users, so yeah, sounds like legit product idea.